
Certificates And Signatures Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Working with the OpenStack Swift Object Store
Swift functions as a distributed, API-accessible storage platform that can be integrated directly into applications or used to store VM images, backups, and archives as well as smaller files, such as photos and email messages. clients can access the API via the Horizon Dashboard or the Ope
From playlist Learn to Master OpenStack today

Signature Validation - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Fundamental concepts of Digital Signatures are discussed. ElGamal and Schnorr Digital Signature schemes are analyzed. Digital signature standard is presented.
From playlist Network Security

Fundamental concepts of Digital Signatures are discussed. ElGamal and Schnorr Digital Signature schemes are analyzed. Digital signature standard is presented.
From playlist Network Security
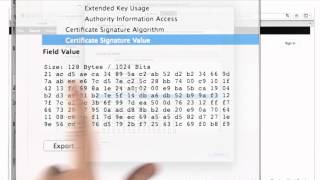
Certificates And Signatures - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Signature Validation Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Trustchain: Decentralised Public Key Infrastructure for Digital Identity
session 7 – Dr Timothy Hobson and Dr Dam Greenbury, The Alan Turing Institute
From playlist Trustworthy Digital Identity – Workshop, December 2022

CERIAS Security: Privacy Policy-driven Access Control with Mixed Credentials 5/5
Clip 5/5 Speaker: Shouhuai Xu · University of Texas at San Antonio Access control in decentralized systems is an important problem that has not been fully understood, except perhaps that it should be based on credentials. There are mainly two research approaches towards this goal: one
From playlist The CERIAS Security Seminars 2005 (2)

TQFTs from non-semisimple modular categories and modified traces, Marco de Renzi, Lecture III
Lecture series on modified traces in algebra and topology Topological Quantum Field Theories (TQFTs for short) provide very sophisticated tools for the study of topology in dimension 2 and 3: they contain invariants of 3-manifolds that can be computed by cut-and-paste methods, and their e
From playlist Lecture series on modified traces in algebra and topology

Proving super-polynomial lower bounds for syntactic multilinear branching programs by Ramya C
Discussion Meeting Workshop on Algebraic Complexity Theory  ORGANIZERS Prahladh Harsha, Ramprasad Saptharishi and Srikanth Srinivasan DATE & TIME 25 March 2019 to 29 March 2019 VENUE Madhava Lecture Hall, ICTS Bangalore Algebraic complexity aims at understanding the computationa
From playlist Workshop on Algebraic Complexity Theory 2019
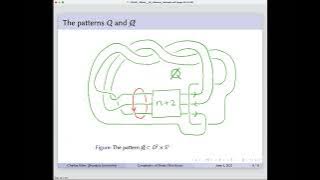
Charles Stine: The Complexity of Shake Slice Knots
Charles Stine, Brandeis University Title: The Complexity of Shake Slice Knots It is a well studied conjecture that a shake slice knot is in fact slice. Many counterexamples have been given, but most are close to being slice in a technical sense. In this talk, we will give a precise way to
From playlist 39th Annual Geometric Topology Workshop (Online), June 6-8, 2022

Live CEOing Ep 403: Cryptography Review in Wolfram Language
In this episode of Live CEOing, Stephen Wolfram reviews upcoming functionality for cryptography features of the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through the official Twitch channel of Ste
From playlist Behind the Scenes in Real-Life Software Design

Stanford Seminar - Persistent and Unforgeable Watermarks for DeepNeural Networks
Huiying Li University of Chicago Emily Wegner University of Chicago October 30, 2019 As deep learning classifiers continue to mature, model providers with sufficient data and computation resources are exploring approaches to monetize the development of increasingly powerful models. Licen
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Markus Banagl : The L-Homology fundamental class for singular spaces and the stratified Novikov
Abstract : An oriented manifold possesses an L-homology fundamental class which is an integral refinement of its Hirzebruch L-class and assembles to the symmetric signature. In joint work with Gerd Laures and James McClure, we give a construction of such an L-homology fundamental class for
From playlist Topology

RailsConf 2021: ho Are You? Delegation, Federation, Assertions and Claims - Lyle Mullican
Identity management? Stick a username and (hashed) password in a database, and done! That's how many apps get started, at least. But what happens once you need single sign-on across multiple domains, or if you'd rather avoid the headache of managing those passwords to begin with? This sess
From playlist RailsConf 2021

Cloud OnAir: Unravel the mystery of container security
Containers are increasingly being used to deploy applications, and with good reason, given their portability, scalability and lower management burden. However, the security of containerized applications is still not well understood. Join this webinar to learn - how container security diff
From playlist Center for Applied Cybersecurity Research (CACR)

CERIAS Security: Privacy Policy-driven Access Control with Mixed Credentials 4/5
Clip 4/5 Speaker: Shouhuai Xu · University of Texas at San Antonio Access control in decentralized systems is an important problem that has not been fully understood, except perhaps that it should be based on credentials. There are mainly two research approaches towards this goal: one
From playlist The CERIAS Security Seminars 2005 (2)
