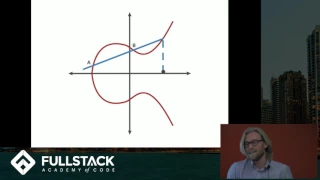
Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange
Learn more advanced front-end and full-stack development at: https://www.fullstackacademy.com Elliptic Curve Cryptography (ECC) is a type of public key cryptography that relies on the math of both elliptic curves as well as number theory. This technique can be used to create smaller, fast
From playlist Elliptic Curves - Number Theory and Applications

When Risk Taking Goes Too Far - The Archegos Collapse
Click the link to sign up to Wise, the world’s most international account: http://bit.ly/coldfusionandwise ColdFusion Discord: https://discord.gg/3WWKmzqMPY --- About ColdFusion --- ColdFusion is an Australian based online media company independently run by Dagogo Altraide since 2009. T
From playlist All My Videos

A.I. Just Designed An Enzyme That Eats Plastic
» Podcast I Co-host: https://www.youtube.com/channel/UC6jKUaNXSnuW52CxexLcOJg » ColdFusion Discord: https://discord.gg/coldfusion » Twitter | @ColdFusion_TV » Instagram | coldfusiontv --- About ColdFusion --- ColdFusion is an Australian based online media company independently run by Dag
From playlist Technology

What Is IPSec Protocols? | IPSec Protocol Explained | Computer Networks Tutorial | Simplilearn
In this video on 'What Is IPSec Protocol?', we will examine the introductory knowledge regarding the processes, features, and working of the IPsec protocol. Along with the various steps involved in establishing a secure network channel for data transmission. Topics covered in this video o
From playlist Networking

Fundamental concepts of IPSec are discussed. Authentication Header is explained. ESP & IKE are analyzed.
From playlist Network Security

Fundamental concepts of IPSec are discussed. Authentication Header is explained. Encapsulating Security Payload (ESP) and Internet Key Exchange (IKE) are analyzed.
From playlist Network Security

Citrix XenDesktop 5 CCA Licensing
More videos like this online at http://www.theurbanpenguin.com In this video we look at licensing of XenDesktop 5 and the licensing server. Even the free Express Edition required licenses. The License server can be shared between XenApp and XenDesktop
From playlist Citrix XenDesktop 5 CCA
More videos like this online at http://www.theurbanpenguin.com if you are looking to make a start with PowerShell this may help you on your way using PowerShell with Citrix XenApp. We look at how you can list command by the module and the associated verb or noun
From playlist Citrix

iExploitTube: Episode 5 Exploiting a remote service with metasploit web to get a VNC remote desktop
Credits go out to iExploitTube, check out the channel: http://bit.ly/9J5pSN This tutorial will show you how to get a remote desktop. For more information check out: http://www.iexploit.org
From playlist iExploitTube

Watch more videos on http://www.brightstorm.com/math/geometry SUBSCRIBE FOR All OUR VIDEOS! https://www.youtube.com/subscription_center?add_user=brightstorm2 VISIT BRIGHTSTORM.com FOR TONS OF VIDEO TUTORIALS AND OTHER FEATURES! http://www.brightstorm.com/ LET'S CONNECT! Facebook ► https
From playlist Geometry