
Pattern Matching - Correctness
Learn how to use pattern matching to assist you in your determination of correctness. This video contains two examples, one with feedback and one without. https://teacher.desmos.com/activitybuilder/custom/6066725595e2513dc3958333
From playlist Pattern Matching with Computation Layer
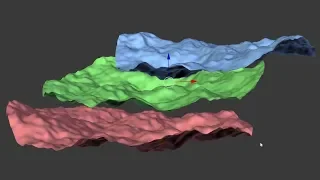
Automatic Pattern Matching for 3D Geometry in Blender
To help refining the alignment of multiple 3D scans with each other, I have written a new tool for Blender which automatically finds the best fit for mesh objects.
From playlist Random Blender Tests
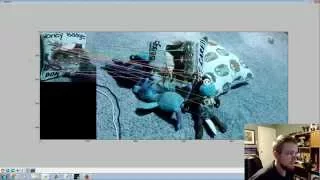
Feature Matching (Homography) Brute Force - OpenCV with Python for Image and Video Analysis 14
Welcome to a feature matching tutorial with OpenCV and Python. Feature matching is going to be a slightly more impressive version of template matching, where a perfect, or very close to perfect, match is required. We start with the image that we're hoping to find, and then we can search f
From playlist OpenCV with Python for Image and Video Analysis
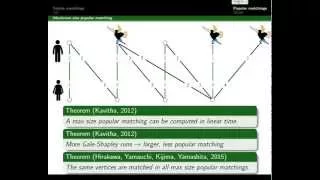
We are given a bipartite graph where each vertex has a strict preference list ranking its neighbors. A matching M is stable if there is no unmatched pair ab, so that a and b both prefer each other to their partners in M. A matching M is popular if there is no matching M' such that the num
From playlist HIM Lectures 2015
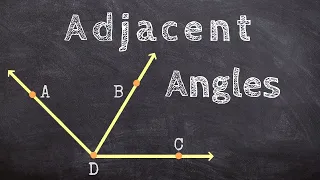
What are examples of adjacent angles
👉 Learn how to define angle relationships. Knowledge of the relationships between angles can help in determining the value of a given angle. The various angle relationships include: vertical angles, adjacent angles, complementary angles, supplementary angles, linear pairs, etc. Vertical a
From playlist Angle Relationships

BlackHat USA 2011: Faces Of Facebook-Or, How The Largest Real ID Database In The World Came To Be
Speaker: ALESSANDRO ACQUISTI Have online social networks created one of the largest databases of identities in the world? We investigate the technical feasibility and privacy implications of combining publicly available Web 2.0 images with off-the-shelf face recognition technology, for th
From playlist BlackHat USA 2011

CERIAS Security: Safely Analyzing Sensitive Network Data 2/6
Clip 2/6 Speaker: Gerome Miklau · University of Massachusetts, Amherst Our recent work investigates the properties of a network that can be accurately studied without threatening the privacy of individuals and their connections. We adopt the rigorous condition of differential privacy, an
From playlist The CERIAS Security Seminars 2009

Best JQuery Book : http://goo.gl/e30dUI This is the first part of my JQuery Video Tutorial. I will also cover all of the techniques that go into implementing a dynamic site using Asynchronous JavaScript and XML (AJAX). Code is Here: http://bit.ly/i3gH6c Article on AJAX Here:http://bit.
From playlist JQuery Video Tutorial

Nexus Trimester - Negar Kiyavash (UIUC)
Privacy-preserving Data Analytics on Social Networks: Limits of De-anonymizablity Negar Kiyavash (UIUC) March 24, 2016 Abstract: Social networks are an integral part of our lives. They provide significant amount of explicit and implicit information about their users. On one hand this dat
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme
Become Anonymous & Untraceable | How To Securely Install & Use Tails | Tor Tutorial
Tails - The Amnesic Incognito Live System, is the most anonymous operating system in the world. Edward Snowden used to leak the NSA documents. Here's how you can get it too. Support me through Patreon: https://www.patreon.com/thehatedone - or donate anonymously: Monero: 84DYxU8rPzQ88SxQqB
From playlist TUTORIALS & HOW TO's

How to use Facebook anonymously | Stop Facebook tracking | Protect yourself from hackers and doxxing
Do you know how to use Facebook anonymously? Facebook tracks you all over the web and to regain your online privacy, you need stop Facebook tracking mechanisms. In this video, you'll learn how to stop Facebook tracking. How much Facebook knows about you? Everything: https://youtu.be/9sFl
From playlist TUTORIALS & HOW TO's

MountainWest RubyConf 2015 - Better Routing Through Trees
by Jeremy Evans This presentation will describe an approach to routing web requests efficiently through the use of a routing tree. A routing tree usually routes requests by looking at the first segment in request path, and sending it to the routing tree branch that handles that segment, re
From playlist MWRC 2015

25c3: Security and anonymity vulnerabilities in Tor
Speaker: Roger Dingledine Past, present, and future There have been a number of exciting bugs and design flaws in Tor over the years, with effects ranging from complete anonymity compromise to remote code execution. Some of them are our fault, and some are the fault of components (librar
From playlist 25C3: Nothing to hide
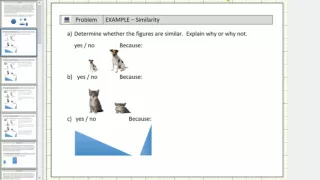
This video introduces similarity and explains how to determine if two figures are similar or not. http://mathispower4u.com
From playlist Number Sense - Decimals, Percents, and Ratios

How To Be Anonymous In The Streets
Support independent research and analysis by joining my Patreon page: https://www.patreon.com/thehatedone The 21st century has erased the relative anonymity of the public square. Street surveillance is so advanced and ubiquitous today that anyone and everyone can be identified and tracke
From playlist TUTORIALS & HOW TO's

Legal Theorems of Privacy - Kobbi Nissim
Computer Science/Discrete Mathematics Seminar I Topic: Legal Theorems of Privacy Speaker: Kobbi Nissim Affiliation: Georgetown University Date: April 13, 2020 For more video please visit http://video.ias.edu
From playlist Mathematics

What is an angle and it's parts
👉 Learn how to define angle relationships. Knowledge of the relationships between angles can help in determining the value of a given angle. The various angle relationships include: vertical angles, adjacent angles, complementary angles, supplementary angles, linear pairs, etc. Vertical a
From playlist Angle Relationships


