
Anomaly Detection for JavaScript Apps
Watch this video to learn about the anomaly detection tools which will enable you to monitor and detect abnormalities in your JavaScript apps. PUBLICATION PERMISSIONS: Original video was published with the Creative Commons Attribution license (reuse allowed). Link: https://www.youtube.com
From playlist JavaScript

Anomaly Detection : Time Series Talk
Detecting anomalies and adjusting for them in time series. Code used in this video: https://github.com/ritvikmath/Time-Series-Analysis/blob/master/Anomaly%20Detection.ipynb
From playlist Time Series Analysis

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Machine Learning for Cyber Security - Session 8
anomaly detection anonmalous events with categorical typically no metric space for comparison how to learn normal vs abnormal , esp with no labels, self-supervised embeddings NCE
From playlist Machine Learning for Cyber Security

Modern Anomaly and Novelty Detection: Anomaly Detection - Session 2
Anomaly detection approaches Anomaly detection techniques Deep learning based approaches
From playlist Modern Anomaly and Novelty Detection

Modern Anomaly and Novelty Detection: Introduction - Session 1
About anomalies Applications Thinking fast and slow
From playlist Modern Anomaly and Novelty Detection
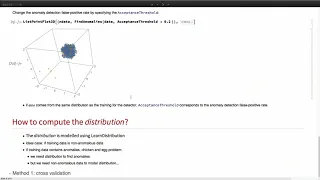
New Unsupervised Learning Functions
To learn more about Wolfram Technology Conference, please visit: https://www.wolfram.com/events/technology-conference/ Speaker: Amir Azadi Wolfram developers and colleagues discussed the latest in innovative technologies for cloud computing, interactive deployment, mobile devices, and mo
From playlist Wolfram Technology Conference 2018

Live CEOing Ep 162: Machine Learning in Wolfram Language
Watch Stephen Wolfram and teams of developers in a live, working, language design meeting. This episode is about Machine Learning in the Wolfram Language.
From playlist Behind the Scenes in Real-Life Software Design

Live CEOing Ep 88: Machine Learning in Wolfram Language
Watch Stephen Wolfram and teams of developers in a live, working, language design meeting. This episode is about Machine Learning in the Wolfram Language.
From playlist Behind the Scenes in Real-Life Software Design

CERIAS Security: Responding to Anomalous Database Requests 1/4
Clip 1/4 Speaker: Ashish Kamra Organizations have recently shown increased interest in database activity monitoring and anomaly detection techniques to safeguard their internal databases. Once an anomaly is detected, a response from the database is needed to contain the effects of the an
From playlist The CERIAS Security Seminars 2008
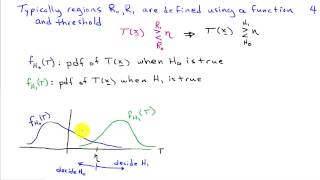
Introduction to Detection Theory (Hypothesis Testing)
http://AllSignalProcessing.com for more great signal-processing content: ad-free videos, concept/screenshot files, quizzes, MATLAB and data files. Includes definitions of binary and m-ary tests, simple and composite hypotheses, decision regions, and test performance characterization: prob
From playlist Estimation and Detection Theory
Introduction to Outlier Detection Methods (Part 2) - Wolfram Livecoding Session
Andreas Lauschke, a senior mathematical programmer, live-demos key Wolfram Language features useful in data science. In this seventh session, the introduction to outlier detection methods continues, and the basics of continuous probability theory are recapped. Then learn about the built-in
From playlist Data Science with Andreas Lauschke



